Enable and overwrite Content Filter
Enable Content Filter
- Content filtering functionality is part of Enterprise Firewall.
- Under Content Filter you have the option to enable Web Filter, Safesearch and Antivirus.
- The Activation of the Content Filter option is done at the VPN level.
Configuration option TLS Inspection
-
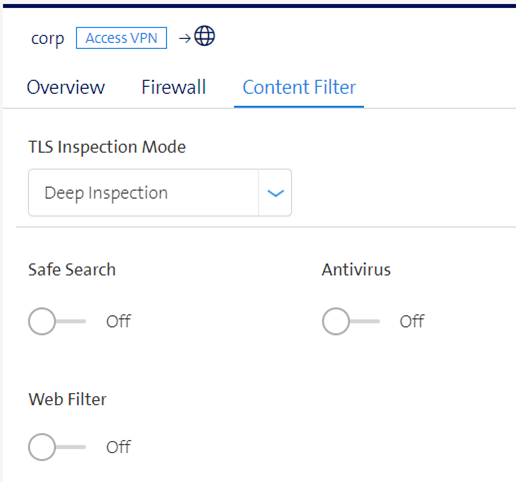
For Security go to Outbound Links / Content Filter
-
First, select TLS Inspection Mode because this selection affects other options such as "Anti-Virus" and Web Filter. Choose between Deep Inspection Mode and Certificate Inspection Mode.
Deep Inspection
- Today, most Internet traffic is encrypted.
- To check the content of encrypted web traffic, the firewall must decrypt it, the decrypted data can then be inspected accordingly.
- After the content filter has filtered the data stream, the connection with the Swisscom certificate is encrypted and forwarded to the client.
- For the client to trust the certificate, this certificate must be installed on the client.
- If you want to enable anti-virus on your firewall, the Deep Inspection option must be enabled.
- Activating Deep Inspection will result in a reduction of network performance.
- This is to be expected as the operations associated with deep inspection are computationally intensive.
- If the performance drop is too high, you have the option to whitelist the websites you trust.
- Deep Inspection will not inspect the URLs listed on the whitelist.
Certificate Verification
- In contrast to Deep Inspection, this option does not break the network packets for inspection, but the firewall only controls the website SSL certificate.
- Devices on which a certificate installation difficult or impossible, this option can be used to create Internet access.
- If a website is blocked according to your category, no splash page appears in the browser.
- "Certificate Verification" does not check web traffic for signs of malware.
- This option allows you to ensure that the Web server you are reaching has a valid certificate.
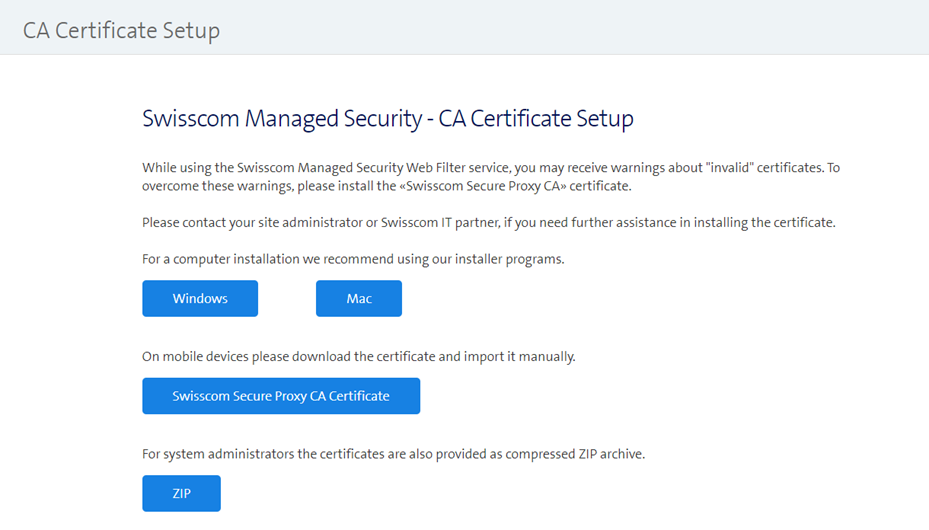
Configuration: Install SSL Certificate for Deep Inspection
- To check the encrypted web traffic, the web filter decrypts the connection and encrypts it with the Swisscom Webfilter certificate.
- The Web Filter Gateway Certificate can be downloaded from this website.
- Attention: To download the certificate, you must be on the LAN where the web filter is enabled.
- The file can be installed on the device (laptop, tablet, etc...) by a user who has local administrator rights on the device (e.g. for Internet Explorer).
SafeSearch
- SafeSearch is an option to filter offensive search results, such as pornographic content, from search engine results.
- SafeSearch does not always work seamlessly.
- However, it may help you to avoid explicit (explicit) and inappropriate search results on your smartphone, tablet or computer.
- SafeSearch covers searches on Google, Chrome and Bing today.
- When you enable SafeSearch in the dashboard, an additional option is appended to the URL or HTTP request to force it into safe mode.
- When SafeSearch is enabled, traffic is TLS-inspected, even if the user has not explicitly selected Deep Inspection under TLS-Inspection.
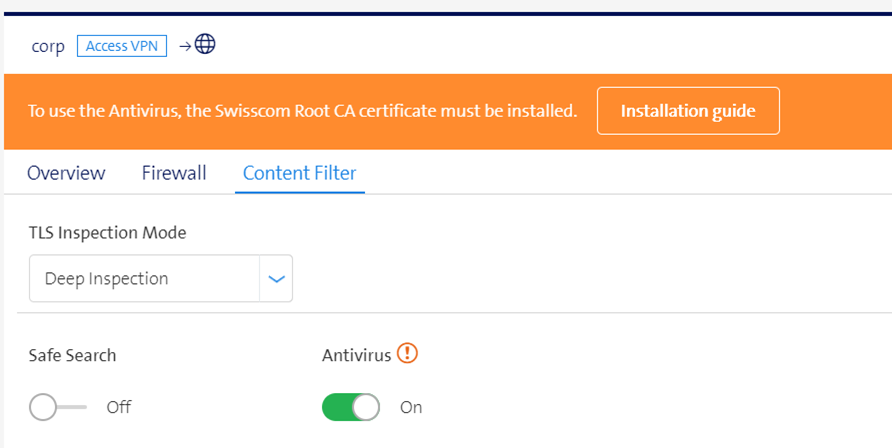
Antivirus
- The Antivirus option scans the contents of web connections for known virus patterns.
- It can be activated in the dashboard under Managed Security > Outbound Links > Content Filter.
- For the Antivirus option, the certificates must be installed and Deep Inspection enabled to verify encrypted connections.
- Once you enable Anti-Virus in the dashboard, you will be prompted to install the certificate on your devices.
- Click Installation Instructions to get step-by-step guidelines for installing the certificates on your devices.
Web Filter
- The Web Filter option requires the certificates to be installed to verify encrypted connections.
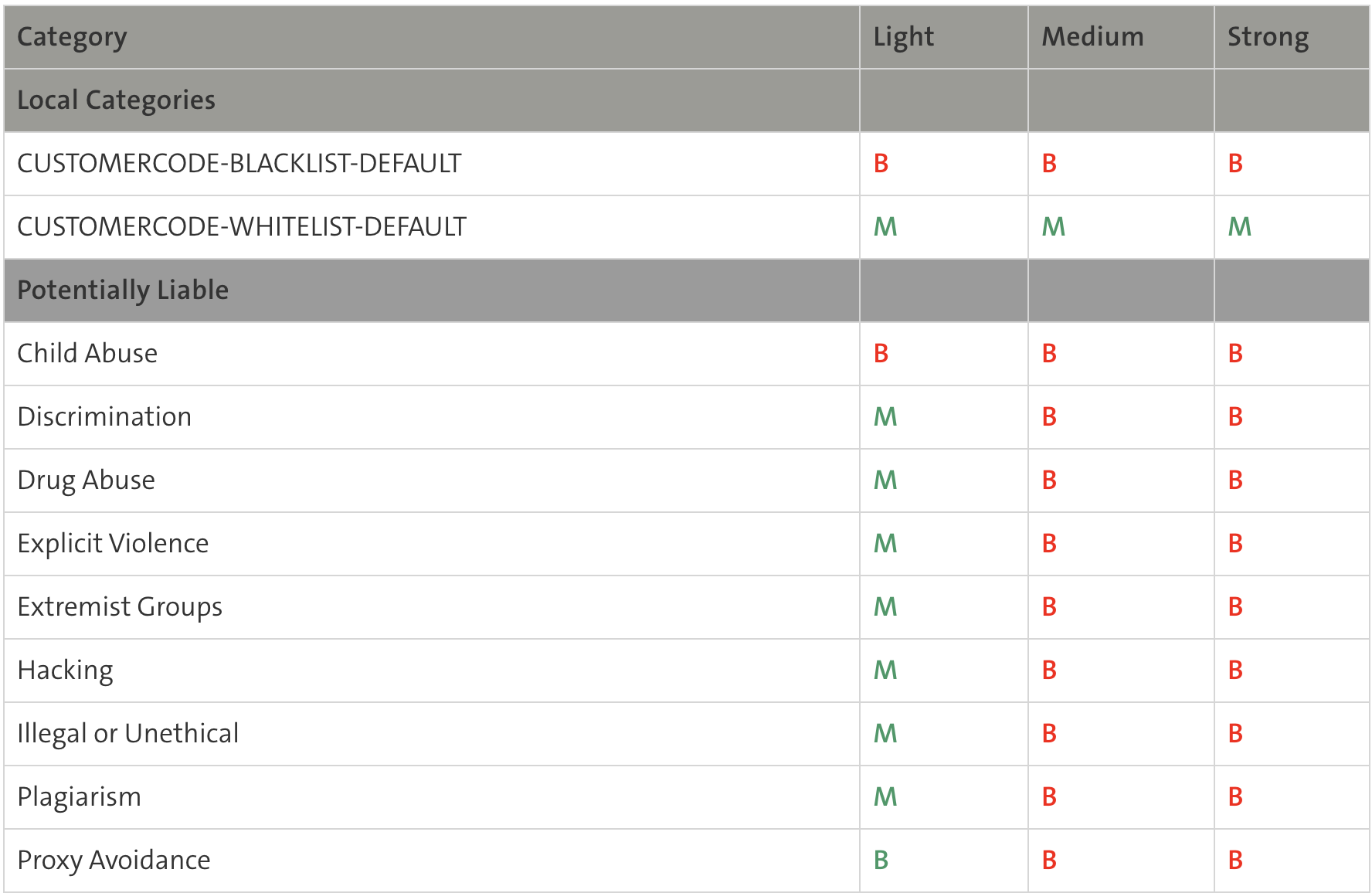
- Here you can select one of the three web filter level templates, Weak / Medium / Strong.
- The predefined Web Filter Ruleset templates are listed in the table below (A= Allow / B=Block / M=Monitor)
B: Traffic is blocked by the web filter. M: The traffic is monitored and is visible in the report. A: Traffic is not monitored and is not visible in the report.
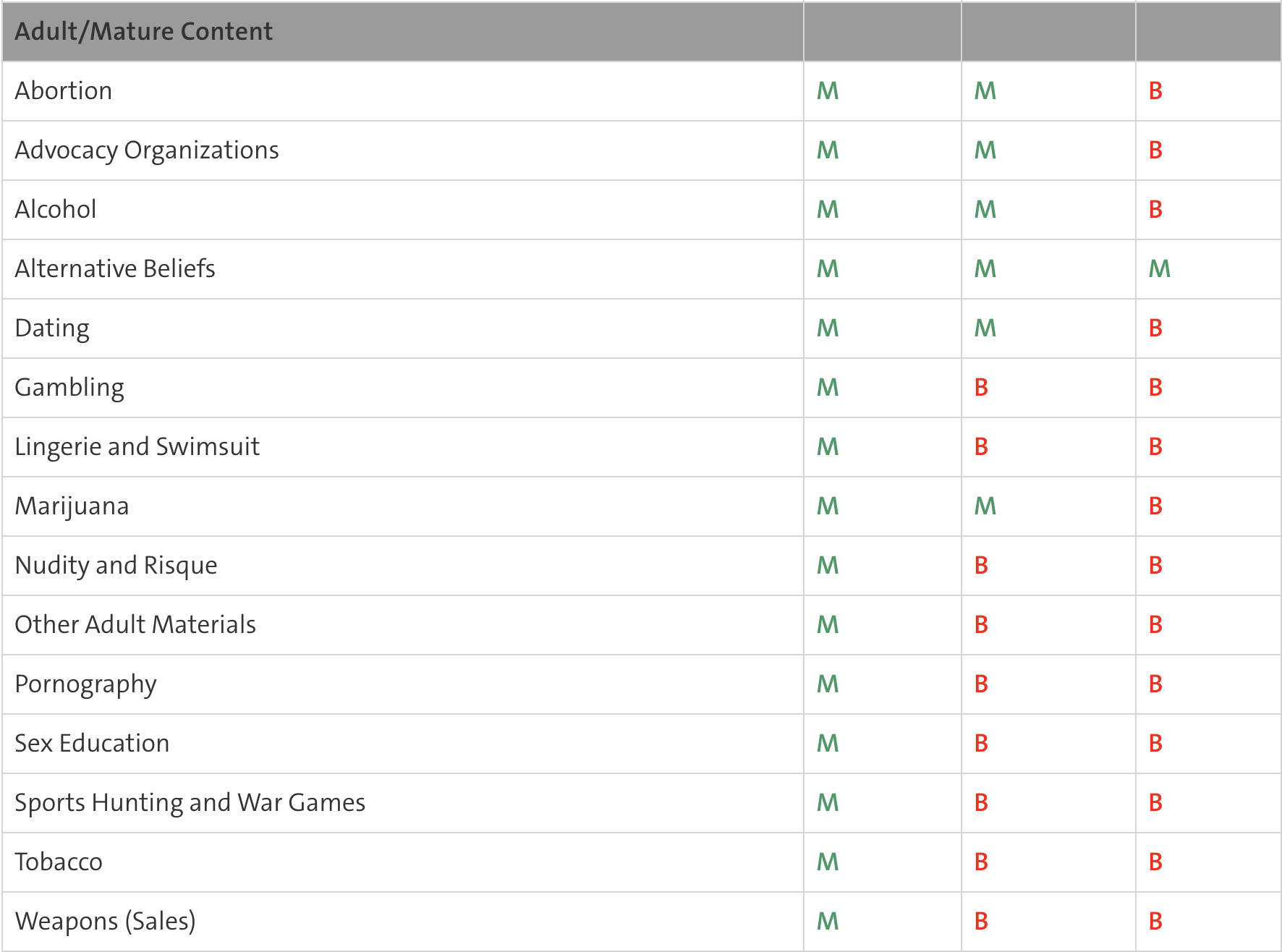
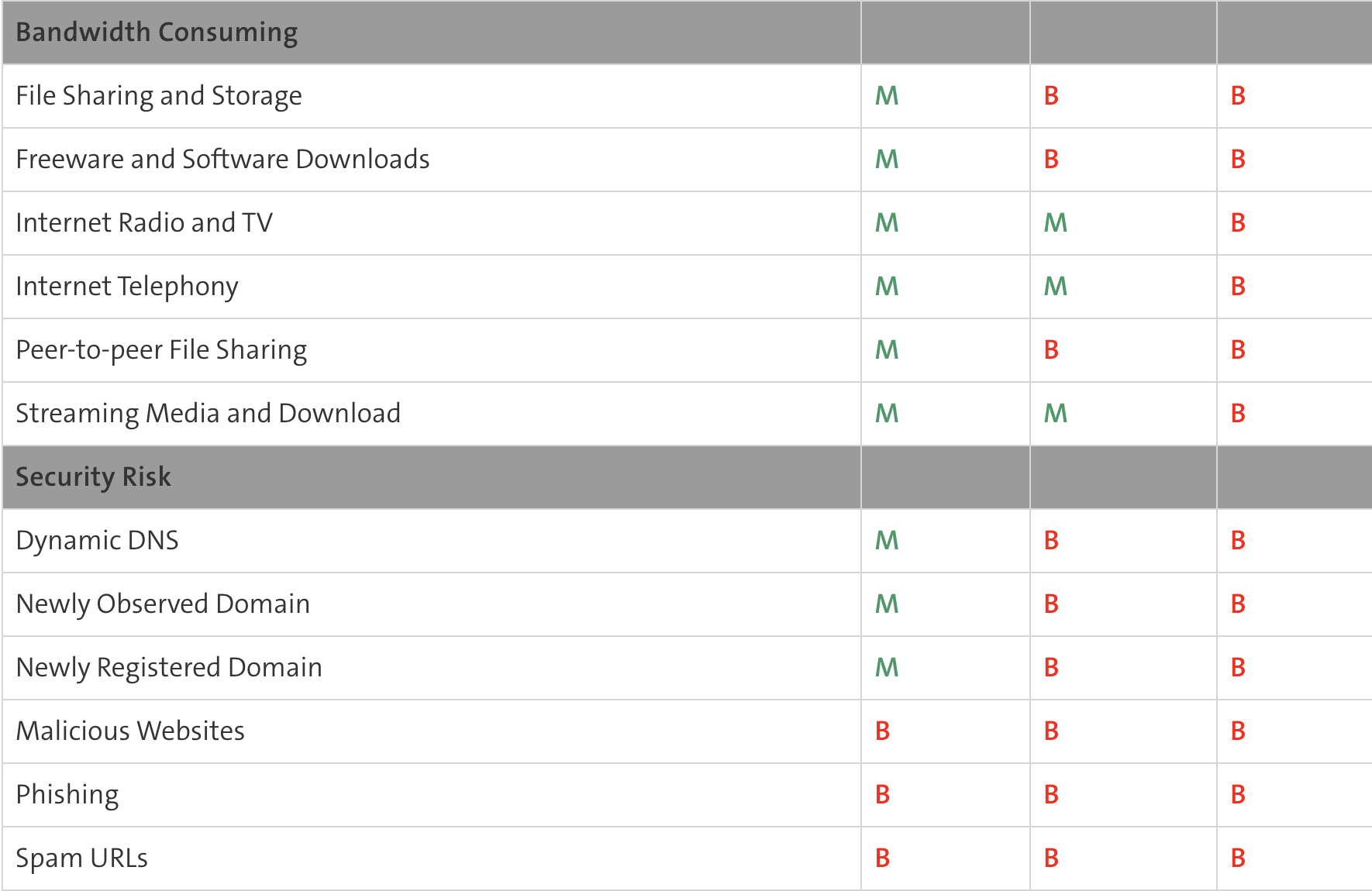
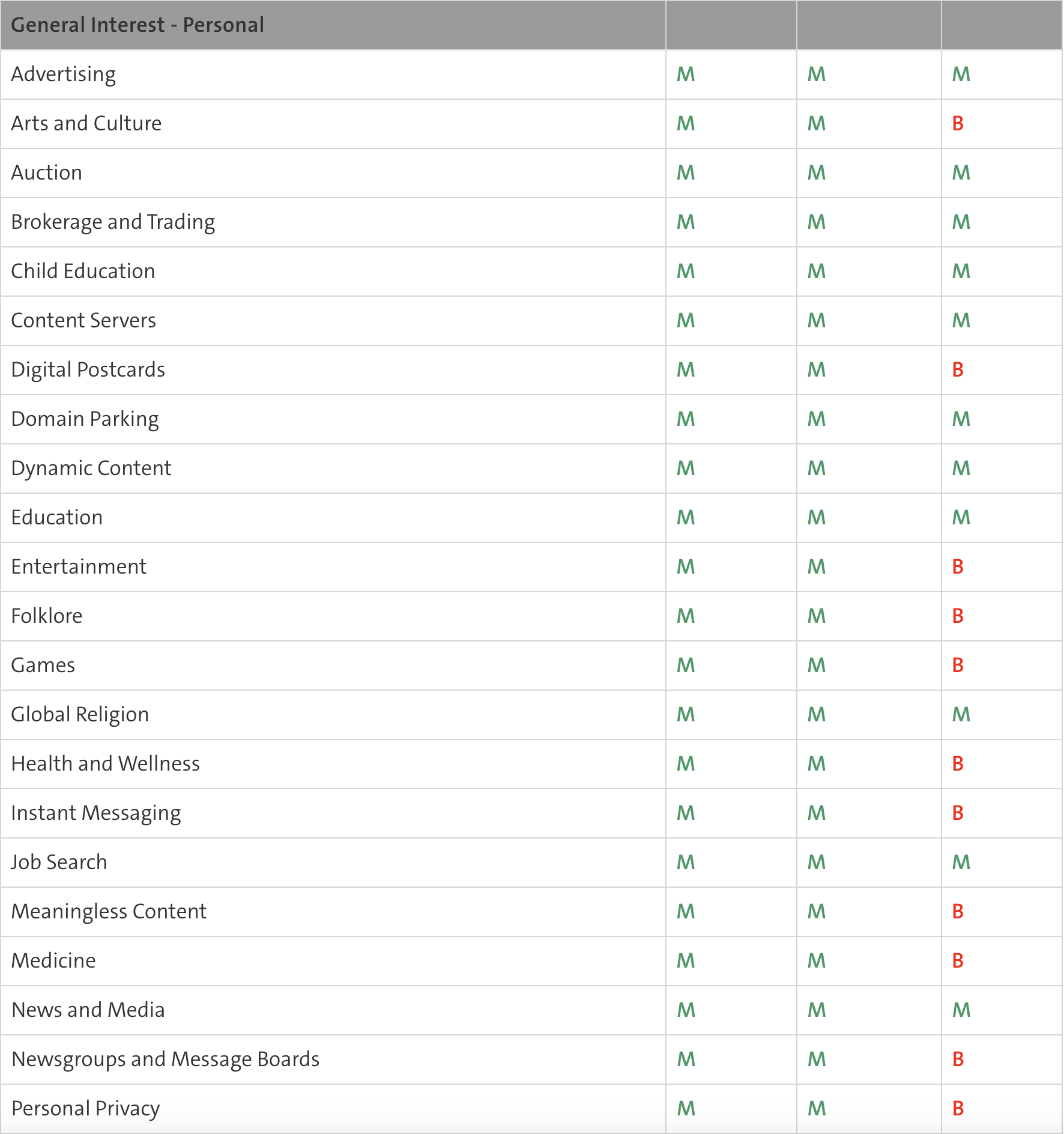
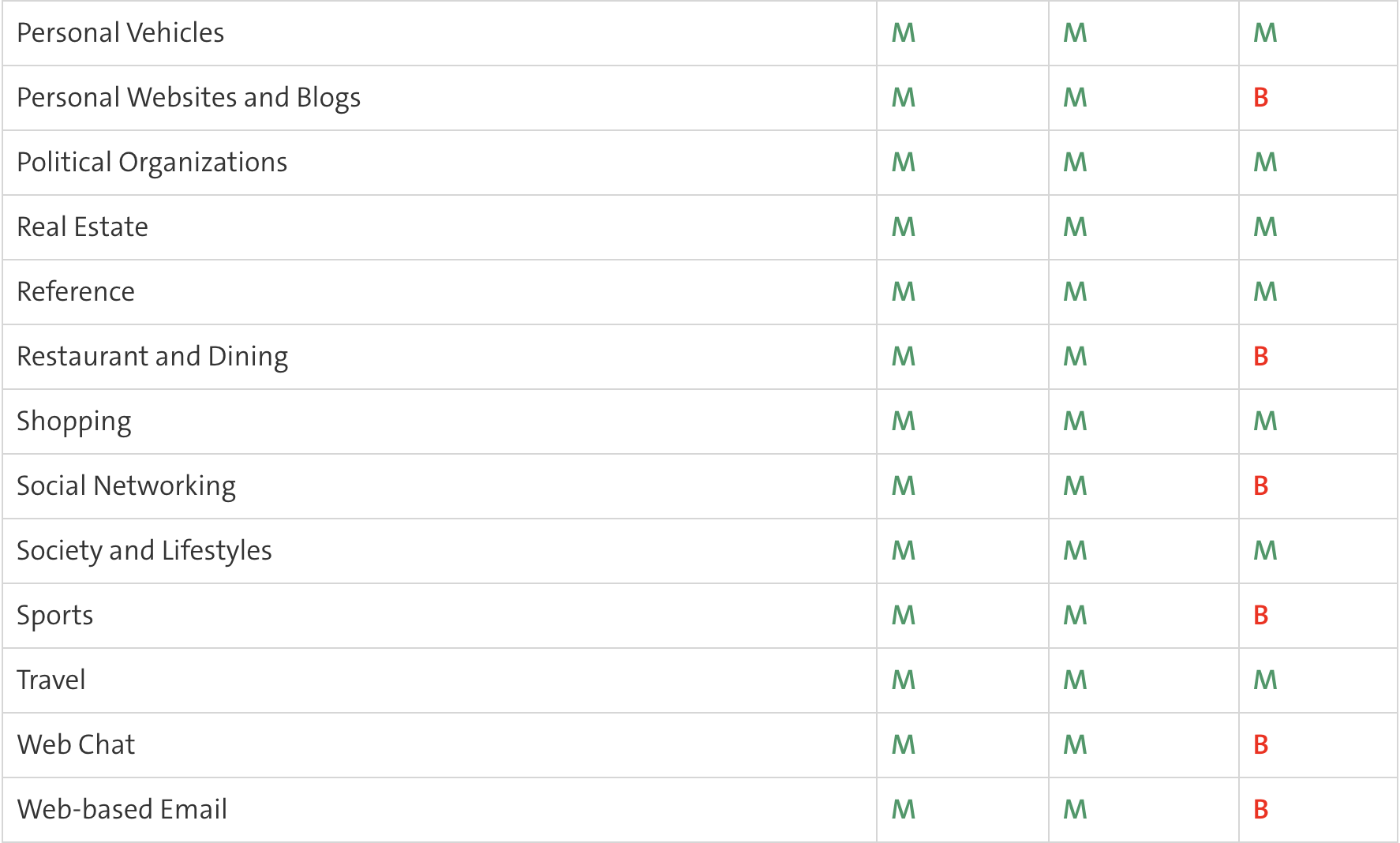
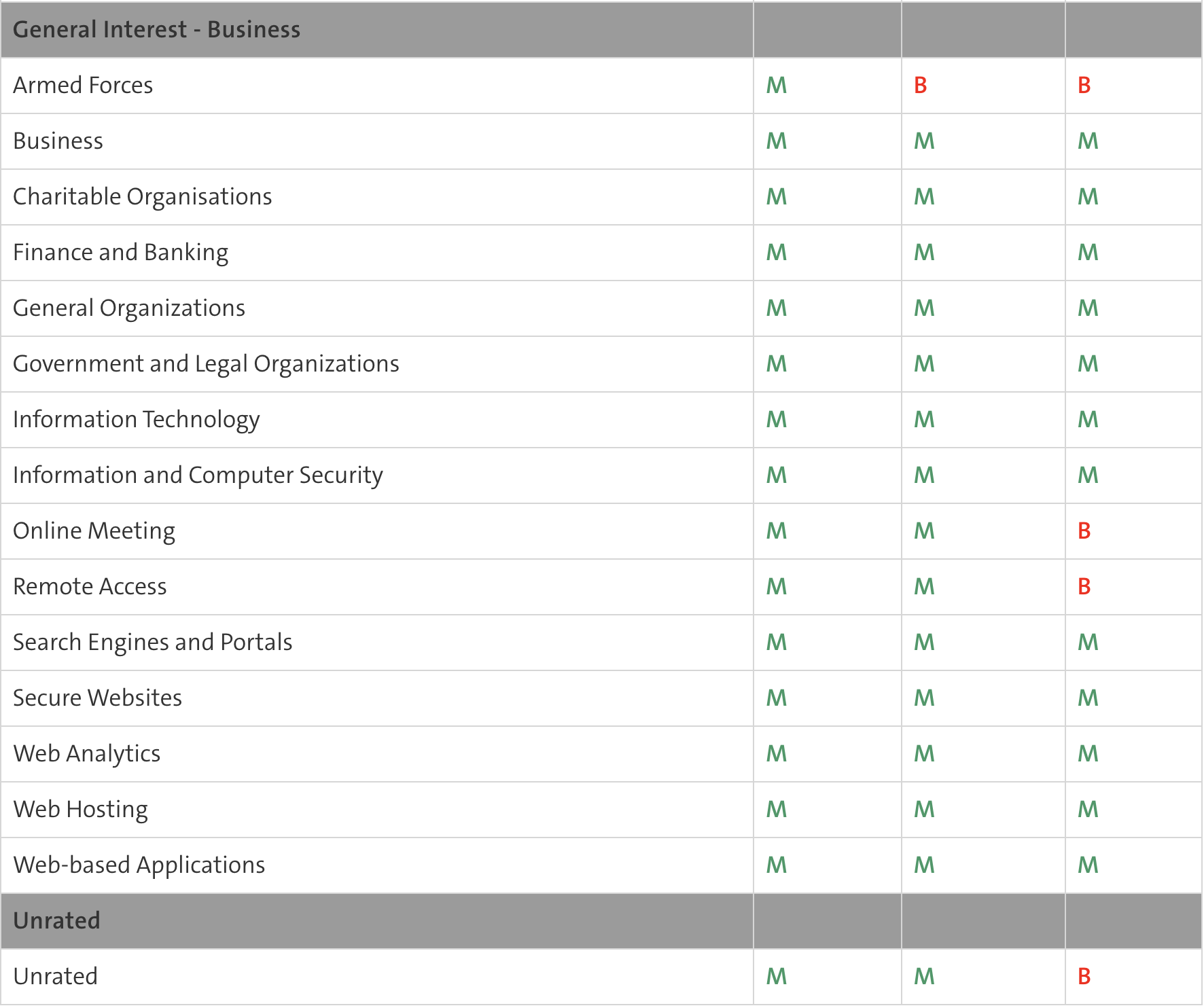
Webfilter Ruleset
- The Web Filter Ruleset can be configured individually in each subcategory based on category.
- Websites of the categories, Banking / Health and Insurance are excluded from the web filter and are not monitored.
Note:
- If you want to enable the web filter, make sure that the firewall rules allow traffic specifically on ports 80 and 443.
- If you want to enable anti-virus, in addition to ports 80 and 443, traffic on ports 25,465,110,143,993,995 should also be allowed.
- Finally, you can enable a global whitelist or a global blacklist here at the VPN level.
- URL filtering does not require an in-depth investigation.
- It can access domain names even in encrypted sessions.
Overwrite Content Filter
- You have the option to override the content filter settings configured on the VPN level.
- To do this, you can activate the setting Content Filter Override on the firewall rule level.
Configuration
-
Select Security > Outbound Links and the corresponding VPN.
-
Then Content Filter Note: If you have previously activated AntiVirus in the global Content Filter settings, you can deactivate http traffic if necessary
-
Override global settings: move the slider to the right to activate it
-
Save the configuration
-
The configuration is activated by sending the shopping cart.
Content filter overrides can be applied to:
- TLS inspection for the ports: 443, 465, 993, 995
- Antivirus for the ports: 25, 80, 110, 143, 443, 465, 993, 995
- Webfilter for the ports: 80 and 443
- Attempting to override the content filter on port 22 does not work